Cyberattacks Sweden 2025 is increasing according to the latest report from Check Point Research. Swedish organizations were exposed to an average of 1791 cyberattacks per week in August, an increase of three percent compared to July. The development points to a growing threat landscape where more and more socially critical activities are becoming targets.
Public sector most exposed
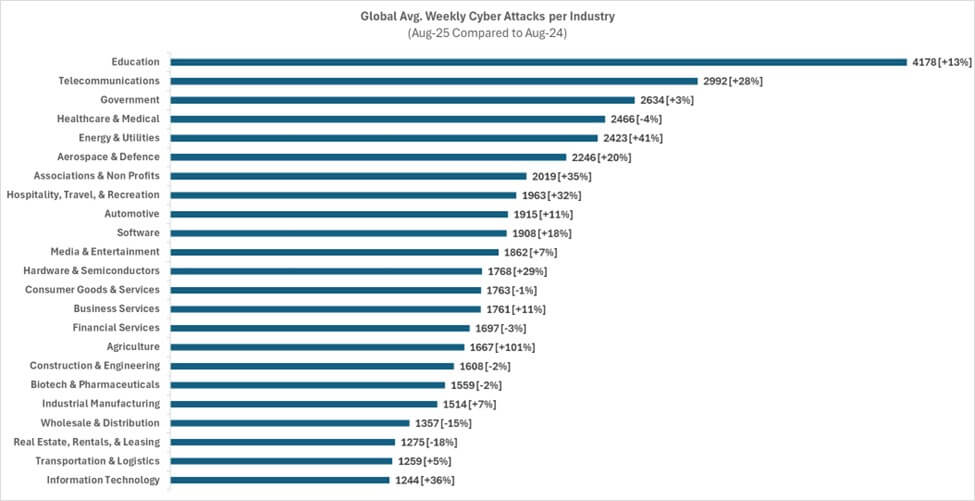
The report shows that the public sector in Sweden was most affected in August 2025This is followed by consulting firms, energy producers, financial companies and the manufacturing industry. Attackers primarily target critical functions, where the impact of an intrusion risks being extensive. Cybercriminals are quickly adapting their methods to exploit areas where digitalization and connectivity have increased sharply in recent years.
Ransomware is on the rise in Sweden
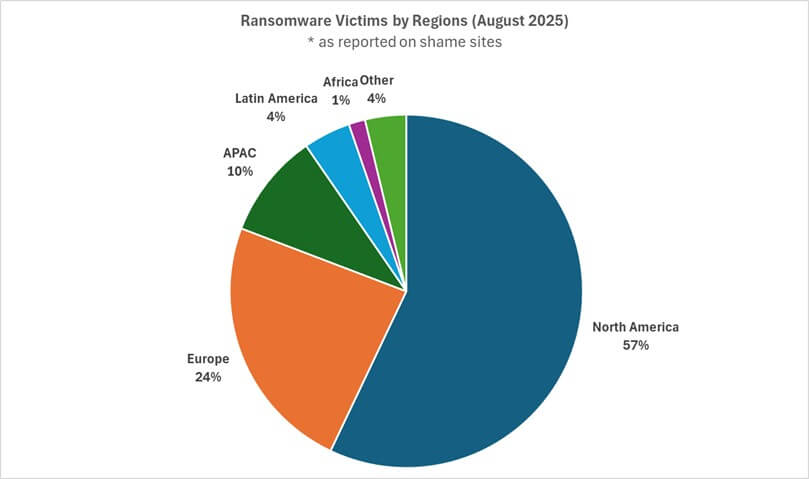
A particularly worrying development is the clear increase in ransomware attacksThis form of attack used to encrypt business data and demand ransoms to restore the systems. For Swedish companies and public actors, this poses a double threat – both economic losses and disruptions in critical services.
Mats Ekdahl, security expert at Check Point Software, comments:
– We see that Swedish organizations are under sustained pressure from attacks. The burden is particularly heavy on the public sector and consulting firms. This places higher requirements for proactive security and rapid action if necessary.
How businesses can protect themselves
To meet the threat posed by Cyberattacks Sweden 2025 shows that organizations need to implement more layers of protection. Among the most important measures are:
- Network segmentation to prevent lateral movement in case of intrusion
- The Zero Trust Principle – where no one user or device automatically considered trusted
- Multi-Factor Authentication (MFA) for stronger identity security
- Advanced protection against phishing to stop the most common intrusion methods
- Monitoring of exposed services, VPN and remote access
- Regular incident management and crisis exercises
- Isolated backups to be able to quickly restore operations in the event of an attack
Consultants and the energy sector at risk
Even if public sector is at the top When it comes to attacks, consultants and energy producers are particularly vulnerable. These players often handle sensitive information and complex IT environments, making them attractive targets. For consulting company this poses a double risk: both that their own systems are attacked and that they used as a springboard for attacks against customers' environments.
Within energy production can cyberattacks lead to major disruptions in electricity supply and societal functions. Here, redundancy, strong segmentation and real-time monitoring are absolutely crucial to ensure operations.
| Region | Avg weekly attacks per org | YoY Change |
| Africa | 3239 | -3% |
| APAC | 2877 | +2% |
| Latin America | 2865 | +6% |
| European | 1685 | +13% |
| North America | 1480 | +20% |
Growing demand for proactive security
The attacks in Sweden follow a global pattern where ransomware and targeted intrusions against critical societal activities increasing in both frequency and complexity. Cyberattacks Sweden 2025 confirms that threats are no longer temporary but a constant pressure that requires security to be prioritized at the management level.
It is no longer enough to simply react to incidents – businesses must build in resilience and resistance right from the start. Organizations that focus on comprehensive protection, from network security to staff training, has the greatest chance of resisting future attacks.
Conclusion
Cyberattacks Sweden 2025 clearly shows that threats against the public sector, consultants and other critical businesses continue to grow. Ransomware is on the rise and attackers are becoming increasingly sophisticated. For Swedish companies and authorities It is crucial to invest in modern security solutions, implement strict security policies and build a culture of preparedness.
For more information, read Check Point Software's blog: https://blog.checkpoint.com/re…
















