Research group Unit 42 at IT security company Palo Alto Networks has exposed an Iranian cyber espionage campaign that used a fake website that was initially copied from the real Mega Model Agency in Germany.
The fake site contained hidden JavaScript code that collected visitors' browser data, including language settings, screen resolution, IP addresses and browser digital fingerprints. The JavaScript code was garbled so that it became unreadable to humans and difficult to detect.

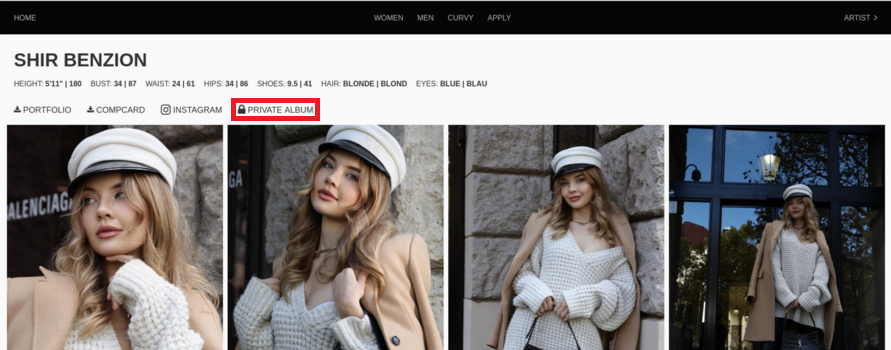
The hackers also posted a fake profile on the site, for a female model named Shir Benzion, with a link to a "private album"It was probably an attempt to trick the visitor into giving up information or downloading malicious code.
Unit 42 has identified the Iranian threat actor Agent Serpens (also known as APT35 or Charming Kitten) as the person behind the campaign. This group conducts cyber espionage through long-term, resource-intensive operations and is considered to be working on behalf of the Islamic Revolutionary Guard Corps in Iran. The same actor has previously targeted Iranian opposition figures, journalists and activists working in exile.

The current operation points to a continued increase in suspected Iranian cyber espionage, including through detailed visitor profiling and sophisticated methods of deception. The activity poses significant risks to organizations and individuals advocating for or supporting the Iranian opposition.
To protect yourself, Unit 42 The advice is to act cautiously when dealing with unsolicited contacts that offer seemingly appealing opportunities. Before responding or sharing sensitive information, information It is important to first ensure the identity and authenticity of contacts, websites and offers.