Jamf Threat Labs has identified a new variant of the malicious code family ChillyHell, a modular backdoor specifically targeting macOS. Despite Apple’s advanced security controls, the threat has managed to go unnoticed and remain openly available online for years. The discovery highlights how quickly cyber threats to macOS are evolving – and how difficult they have become to detect in a timely manner.
Discovery of the new variant
In the recently published report ChillyHell: A Deep Dive into a Modular macOS Backdoor Jamf Threat Labs describes how a new ChillyHell variant uploaded on VirusTotal – a platform where files are analyzed against hundreds of antivirus programs. Despite the file contained advanced malware code, it was initially not marked as dangerous by established antivirus solutions.
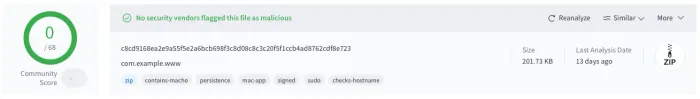
It also turned out that the same code had already 2021 managed to pass Apple's security checks, which means that it could have been active and unsuspected for several years before its discovery in 2025.
Background of the threat
ChillyHell documentation dates back to 2023, when the threat was first linked to an attacker group targeting Ukrainian officials. The modular design of the code makes it particularly dangerous – it can be easily adapted to:
- Give remote access to infected systems.
- Download additional malware in several steps.
- Implement bruteforce attacks on passwords.
Reports also confirm that the code has been openly published on Dropbox since 2021, further underscoring the long-term presence of the threat.
Tactics that bypass protection
ChillyHell uses unusual and sophisticated methods to evade detection:
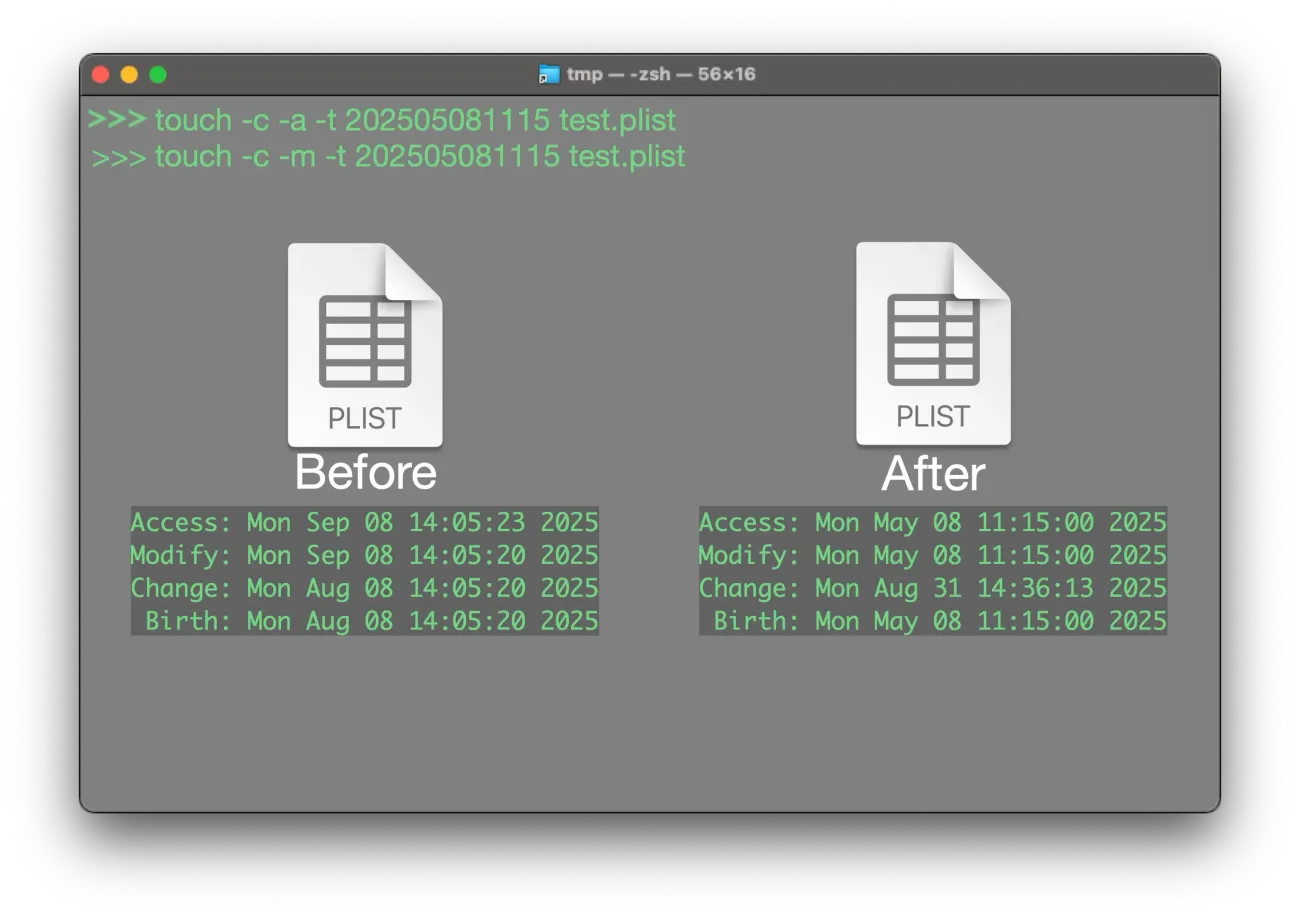
- Time stomping: manipulation of timestamps to hide malicious files.
- Dynamic C2 protocols: the ability to switch between multiple command-and-control channels.
- Flexibility and modularity: making it difficult for traditional security solutions to block the threat permanently.
According to Jamf Threat Labs, the threat was discovered during a routine analysis on VirusTotal, when researchers were able to identify anomalous processes and behavior patterns that indicated something unknown.
Comment from Jamf
“This type of discoveries show the need for strengthened security practices for macOS users"Even seemingly secure systems can contain backdoors that have gone under the radar for years," says Peo Strindlund on Jamf.
The importance of cybersecurity
The discovery of ChillyHell is a reminder that the threat landscape for macOS is constantly changing. A backdoor that managed to evade both Apple's security filters and antivirus software for several years shows how important it is for companies to complement with specialized security solutions.
Jamf Threat Lab's work also demonstrates the value of proactive analyses, where researchers can use advanced methods to identify threats that would otherwise have remained invisible.
About Jamf Threat Labs
Jamf Threat Labs consists of a global team of threat researchers and cybersecurity experts which focuses on analyzing and documenting emerging threats to macOS and mobile platforms. By publishing their findings, they raise awareness among both businesses and individuals, while helping organizations develop better security practices.
















